Hi, I am Damian
Passionate Computer Science graduate. Currently working on my Master's thesis in the field of Artificial Intelligence and Machine Learning, and try-harding OSEP certification. 👨💻☕
About
If you are looking for a potential new member of a red team / penetration testing team, I am a person who is always willing to consider new carrer paths. I not only have a great technical background (education, certifications, experience, interests), but I am also very open to people and communicative, thanks to which every member of my team is always happy with the work done and everyone gets a personal feedback. Additionally, I believe that work should be effective and enjoyable, so in every team I have been in so far I have managed to improve internal and external processes in some way, bigger or smaller, and automate several of them. 🥷
Some of the technologies and tools that I have dealt with so far:
- - Programming Languages: C++, C, Python, Bash, Assembly, Java, Powershell, .NET, [...]
- - Security Tools: nmap/rustscan, Burp-Suite/ZAP, Wireshark, FFUZ, Metasploit, mimikatz, Bloodhound, [...]
- - Technologies: Azure, Git, Docker, JIRA, Kubernetes, Cisco, Qualys, Fortinet, [...]
Looking for an opportunity to work in a challenging position combining my Social and Engineering skils, interesting experiences, and problem-solving mind.
Experience
- Penetration testing of web services, applications, infrastructure according to client and business standards.
- Team leader of penetration tests.
- Detailed reporting of found security issues and ensuring high quality reports as a Quality team member.
Tools: Burp Suite Pro, nmap, wireshark, nessus, FFUZ, SAP GUI, VSC, and many more
- I was responsible for quality and security assurance of delivery by independently auditing projects and engagements.
- Managed Client Data Protection process and supported/hosted client audits and regulatory inspections.
- Provided help with the merger of Objectivity and Accenture on the Objectivity side, including the transfer of cloud environments and the internal Roll-On/Roll-Off process for employees of my former company.
- Designed the security architecture of cloud and hybrid solutions
- Performed various security operational tasks, e.g., incident response, alert fine-tuning, configured security systems, gathered security indicators, helped with ISO 27001 certification
- Created documentation and designed internal security audits, penetration tests, company-wide phishing simulations that raised the awareness of all employees
- Carried out vulnerability scans in internal/external projects and supervised Vulnerability Management in the company
Tools: Microsoft Azure Cloud, 365 Defender, Qualys, Jira, Powershell, Kiuwan
Education
Master of Science in AI and Machine Learning [CURRENTLY]
Wroclaw WSB Merito University in Poland
Expected end date: January 2026
- Machine Learning in practice
- Introduction to deep Machine Learning algorithms
- Computer vision
- Text data analysis using Artificial Intelligence
Relevant Courseworks:
Bachelor of Science in Computer Science
Gdansk University of Technology in Poland
Specialization: Computer Systems
End date: January 2024
- Programming Languages
- Computer Architectures
- Algorithms and Data Structures
- Artifical Intelligence
- Software Engineering
Relevant Courseworks:
Information and Communication Technology Technician
Computer Science Technical High School in Gdansk, Poland
Specialization: Computer Networking
End date: June 2020
- Computer Networks
- Basics of Programming
- Operating Systems
Relevant Courseworks:
Certificates
Projects
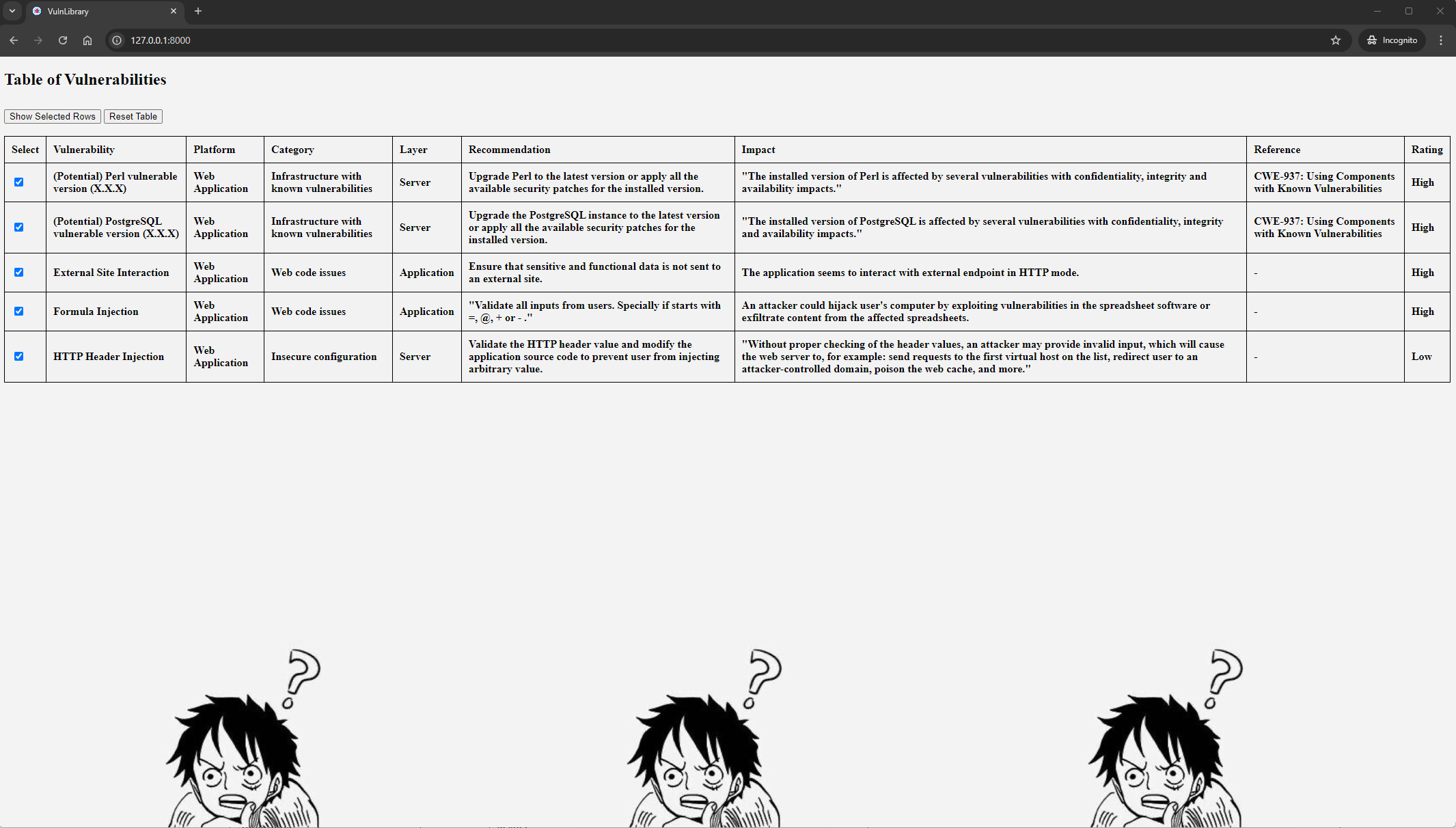
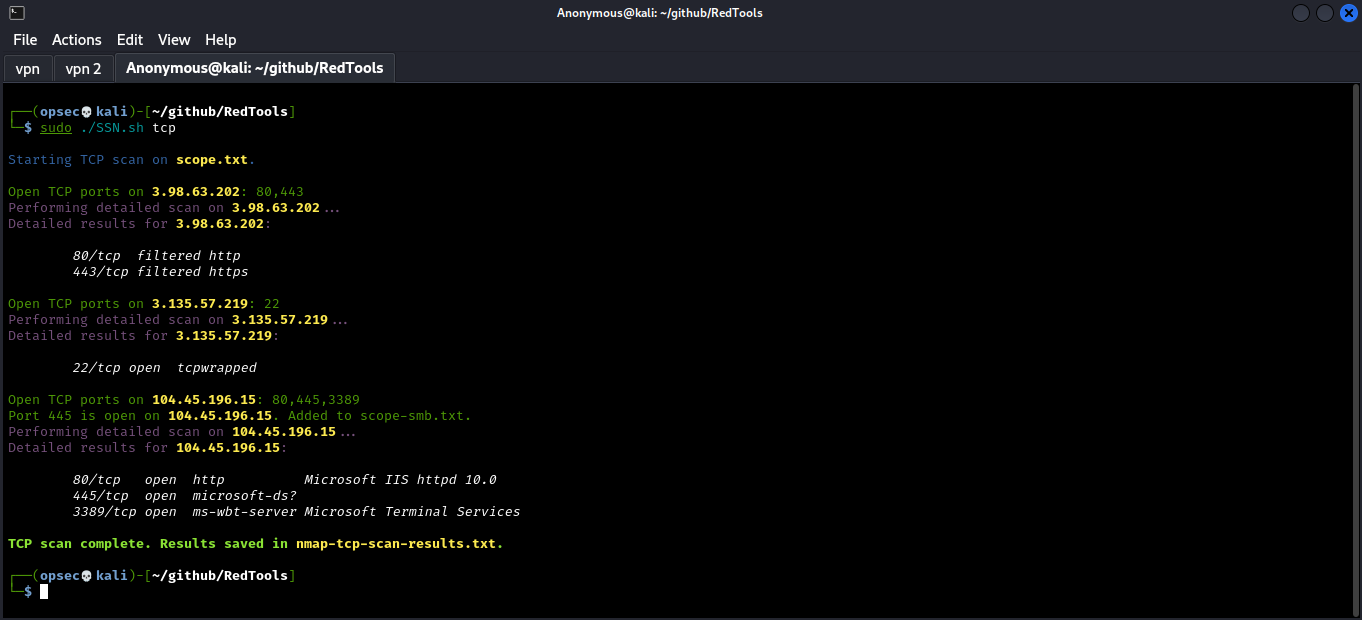
This repository serves as a comprehensive database for tracking and documenting vulnerabilities across various categories.
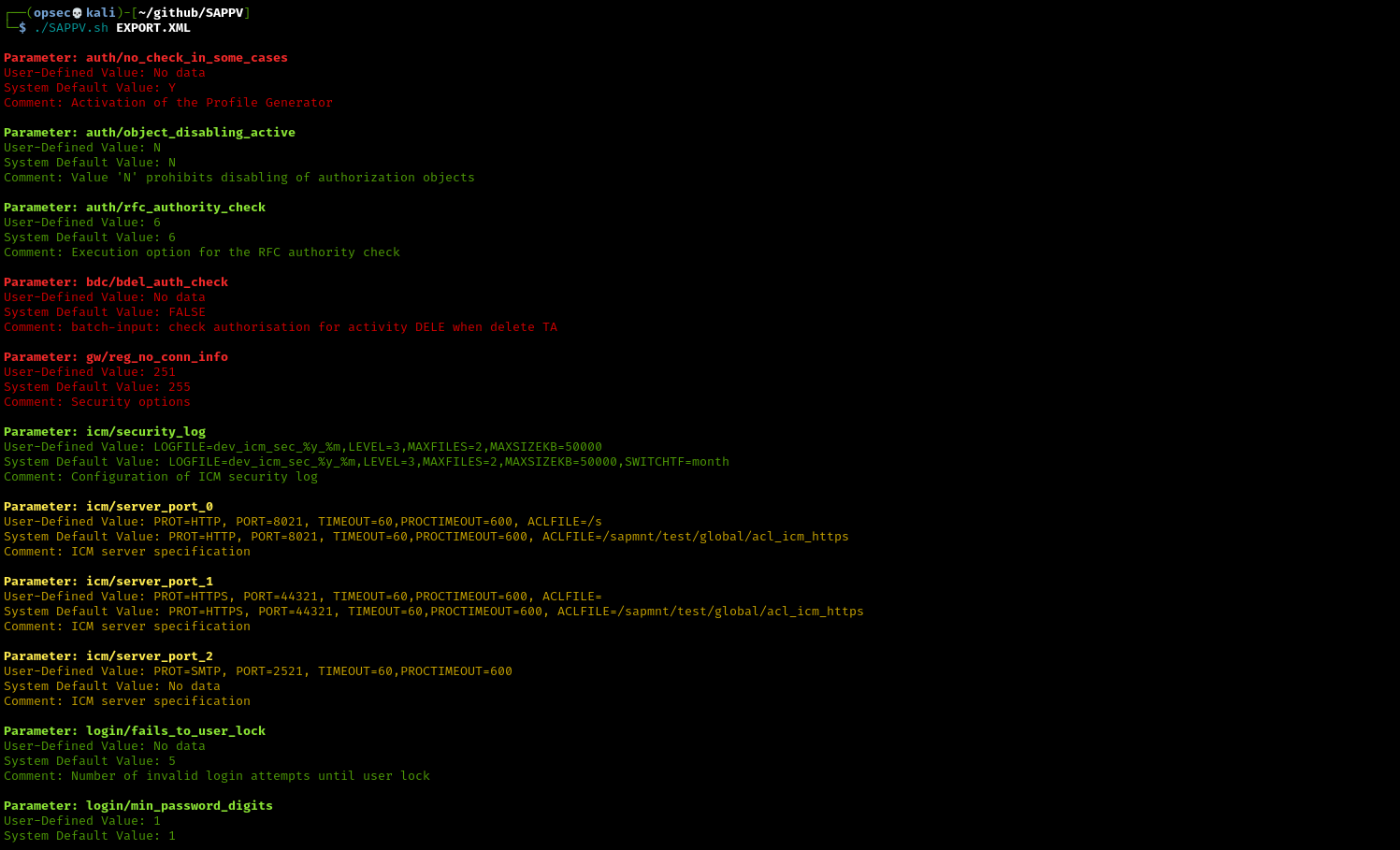
Script-based tool designed for the analysis and validation of SAP configuration parameters.
- Parameter Extraction: Extracts configuration parameters and their values from SAP XML configuration files.
- Validation Rules: Checks values against predefined criteria, such as expected values or ranges, and highlights discrepancies.
- Customizable Parameters: Easily configurable with a list of parameters to check, allowing for flexible and comprehensive configuration analysis.
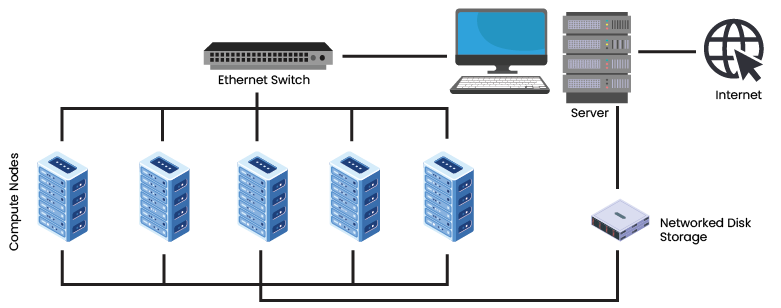
Synchronize metrics downloaded from different nodes in a computing cluster.
- I've organized communication with the client, created and supervised the backlog and code (styling, fixing, refactoring), and successfully delivered the product.
- Universal function to fetch all system metrics, implementing Intel RAPL, NVIDIA NVML libraries.
Books

This book provides knowlkedge on the basics of configuring network devices. The reader will learn network-related technologies such as: TELNET, SSH, FTP, EMAIL, DHCP, DNS and routing protocols RIP, EIGRP, OSPF. Additionally, we have added section on how to design and deploy virtual VLAN networks.
Skills
Programming Languages
 C/C++
C/C++
 Python
Python
 Assembly
Assembly
 Shell Scripting
Shell Scripting
 HTML, CSS, JS
HTML, CSS, JS
 Java
Java
Tools
 Visual Studio
Visual Studio
 nmap, rustscan
nmap, rustscan
 Burp Suite, ZAP
Burp Suite, ZAP
 Wireshark
Wireshark
 Metasploit
Metasploit
 Splunk
Splunk
Other
 Git
Git
 Azure
Azure
 Microsoft Defender
Microsoft Defender
 MITRE ATT&CK
MITRE ATT&CK
 OWASP
OWASP
 Qualys
Qualys